It started like any other morning: you wake up in a cold sweat, realizing your home network is basically a digital Wild West. A simple flat network? Please. When you’ve got a horde of IoT devices and questionable gadgets running around, it’s time for a serious intervention. You sprint to Best Buy, emerge clutching a brand-new managed switch – a purchase that’s probably going to end up on your credit card statement and in a regretful daydream. You painstakingly configure VLANs, hoping to create a digital fortress. You connect to the management page, convinced you’ve finally wrestled control from the chaos. But here’s the thing: cheap consumer-grade switches are notorious for being… well, let’s just say they’re not exactly built for high-security operations. This post will explore the slightly terrifying reality of consumer grade managed switches: even with the best intentions, you might be building a digital castle made of sand.

Experiment: Static IP to Bypass Firewall Rules
Let’s kick things off with a little experiment – and trust me, it’s going to be delightfully unsettling.
- Locate the Web Portal: You’ll likely already know the address of your managed switch’s web portal. We’ll document this for reference.
- VLAN Access Verification: Test access to a VLAN that should have access to the switch’s management page to verify proper operation.
- VLAN Isolation Setup: Configure or select a VLAN and block all access to the managed switch. Blocking internet access is also an option. This VLAN should have a DHCP configuration outside the managed switch’s IP range.
- Network Connection Test: Connect your computer to the network jack currently assigned with that VLAN ID. Ensure you do not have access to the managed switch web portal. If you do, you’ll need to review your firewall rules.
- Manual IP Address Configuration: Set your computer to an IP address within the subnet of the switch. Ensure you do not set your computer to the same IP address as the switch (e.g., if the switch is 192.168.1.5, set your computer to 192.168.1.6). NOTE: This is different from the subnet automatically assigned to this port by the DHCP server.
- Access the Management Page: Connect to the switches management page. It should load up as it did in step 2.
Pretty wild, right? What’s even crazier is that there’s absolutely nothing you can do to prevent clients downstream of your switch from accessing this management page. It’s a fundamental flaw – a glaring vulnerability that underscores how easily networks can be compromised. And the worst part is, many of these devices lack basic logging capabilities, meaning you might never even know a rogue client is attempting to access your network.
You might be thinking: ‘I trust all the devices on my network, so this won’t be a problem.’ But IoT devices often lack robust security controls. They can dynamically change their IP address settings – a vulnerability that could be exploited without administrative rights. More critically, with no failed login logs, these devices could be relentlessly attempting to brute-force your password 24/7. Suffice to say: use a strong, randomly generated username and password.
While there’s no foolproof way to eliminate this vulnerability entirely, it doesn’t mean you shouldn’t implement additional security measures. Like most aspects of security, achieving complete protection is rarely possible. The most important goal is to make your network a more difficult target.
Even though a direct access to the management page might be possible in this scenario, adding simple barriers can significantly reduce the risk. For example, restricting access to the management page from most clients can create a valuable layer of defense against trivial exploits. While this switch might not be suitable for a large corporate network, implementing network isolation controls can dramatically improve your overall security posture.
Experiment 2: Discovering A Switches IP
You may be thinking, ‘Yeah, they might be able to attempt to login if they know the switch IP, but I have a unique IP set so they won’t be able to find it.’ Unfortunately, that’s likely not true. Cheap network switches often respond to Ethernet broadcasts – messages sent to all devices on the network, regardless of VLAN ID. This means any device connected to the switch can discover the switches management IP and initiate a login attempt, effectively bypassing your intended security measures.
- Install Discovery Software: Research your network switch to see if it offers a discovery tool, such as the Easy Smart Configuration Utility for TP-LINK or the NETGEAR Discovery Tool for NetGear.
- Install and Test: Install the chosen software on an unprivileged network device or, if necessary, move the device to an unprivileged port after installation.
- Verify IP Address: Observe the device’s IP address and compare it to the switch IP address used in the first experiment.
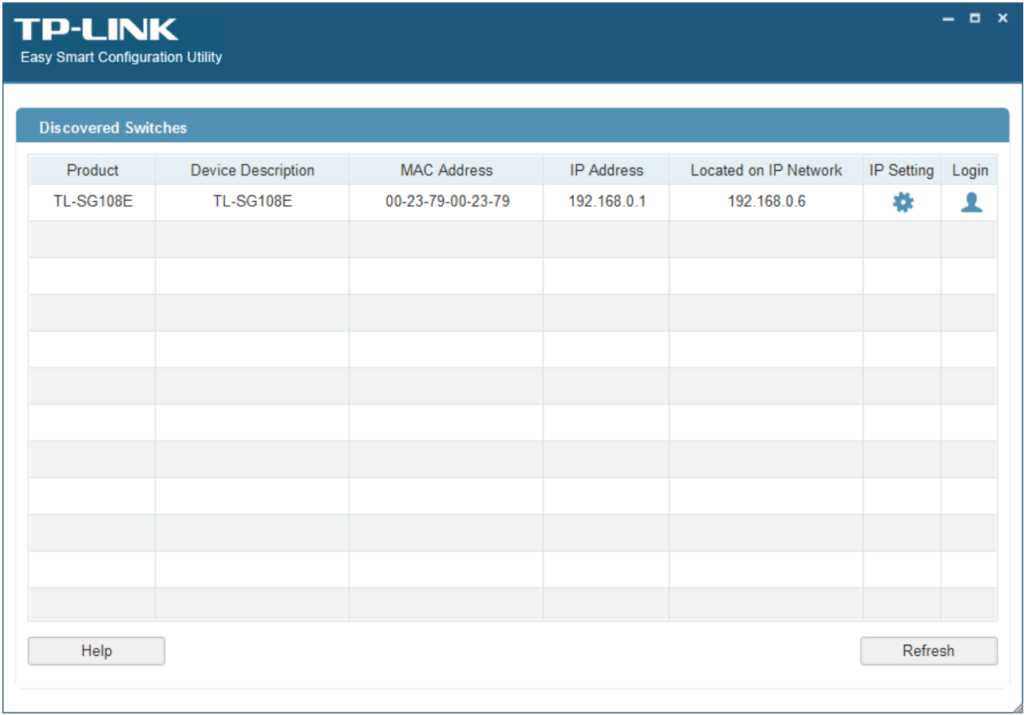
It’s a concerning situation. A rogue client can discover your switch’s IP address, connect to the management portal, and attempt to brute-force your password – all without your knowledge. For those with a technical background, we can investigate this further. Using tools like Wireshark, we can capture and analyze the network traffic to identify the data being exchanged during the discovery process. I’ve already performed this analysis on my TP-LINK switch and will share the captured data below.
Binary data sent from Easy Smart Configuration Utility:
5d 74 6a 04 7d be b0 b2 a9 3f 06 3a 4f 4a 7c 4e 42 2b a2 f5 d7 8b ae ed 50 8f 46 3d c2 02 90 9a a4 ec 81 c6Response from switch:
5d 76 aa 02 be c9 de 3d a9 3f 06 3a 4f 4a 7c 0f 42 2b a2 f5 d7 1b ae ed 50 8f 46 3d c2 02 90 9a 5b 12 81 ca 73 66 06 65 0e e8 70 86 92 04 2c 24 59 73 4c 26 2b 02 b6 24 7f 25 46 39 45 a5 b7 9b 54 2d fd ba 7b e3 ab c4 e2 aa 4c 07 27 3e 1b 9e 9a a8 dc 84 9c 67 98 ac e2 a3 ad aa 8d b7 cd 78 24 9a 39 29 dc df bf eb 09 d6 d3 c9 c4 80 8d 09 4e b7 eb ee 49 ef ee a0 c3 84 34 f2 b6 f6 d3 19 e1 f9 86 5f a4 50 2e 68 8a f2 03 39 85 15 af e3 dd cb 90 0f b9 f1 78 7a b6 74 1b e5 7d 07 a2 ef 1b 2a 01 ae 96 0d e2 5b 72 af 92 a1 ce 18 dc 6d 1e 1b 7f f7Honeypot?
If you’re like me, the immediate reaction might be, ‘Okay, I can’t fully protect myself from this.’ But that doesn’t mean we can’t take action! Here’s some Python code to get you started on building a monitoring system – it’s a first step towards alerting you if someone attempts to exploit this vulnerability. Please note: this is a basic framework and requires further development.
Mimic Easy Smart Configuration Utility
from socket import *
import sys
import time
import random
# Create a UDP socket
serv_sock = socket(AF_INET, SOCK_DGRAM)
serv_add = ('', 29809)
serv_sock.bind(serv_add)
sock = socket(AF_INET, SOCK_DGRAM)
sock.setsockopt(SOL_SOCKET, SO_REUSEADDR, 1)
sock.setsockopt(SOL_SOCKET, SO_BROADCAST, 1)
sock.settimeout(5)
server_address = ('255.255.255.255', 29808)
message = bytearray.fromhex('5d 74 6a 04 7d be b0 b2 a9 3f 06 3a 4f 4a 7c 4e 42 2b a2 f5 d7 8b ae ed 50 8f 46 3d c2 02 90 9a a4 ec 81 c6')
try:
while True:
# Send data
message[15] = random.randrange(0,255)
sent = sock.sendto(message, server_address)
print(message[15])
# Receive response
print('waiting to receive')
data, address = serv_sock.recvfrom(4096)
print(str(address))
print(data.hex(' '))
print(len(data))
finally:
sock.close()Mimic TP-LINK Switch Response
from socket import *
import sys
serv_sock = socket(AF_INET, SOCK_DGRAM)
serv_add = ('', 29808)
sock = socket(AF_INET, SOCK_DGRAM)
sock.setsockopt(SOL_SOCKET, SO_REUSEADDR, 1)
sock.setsockopt(SOL_SOCKET, SO_BROADCAST, 1)
response_add = ('255.255.255.255', 29808)
serv_sock.bind(serv_add)
naunce = bytearray.fromhex("00")
response = bytearray.fromhex('5d 76 aa 02 be c9 de 3d a9 3f 06 3a 4f 4a 7c 0f 42 2b a2 f5 d7 1b ae ed 50 8f 46 3d c2 02 90 9a 5b 12 81 ca 73 66 06 65 0e e8 70 86 92 04 2c 24 59 73 4c 26 2b 02 b6 24 7f 25 46 39 45 a5 b7 9b 54 2d fd ba 7b e3 ab c4 e2 aa 4c 07 27 3e 1b 9e 9a a8 dc 84 9c 67 98 ac e2 a3 ad aa 8d b7 cd 78 24 9a 39 29 dc df bf eb 09 d6 d3 c9 c4 80 8d 09 4e b7 eb ee 49 ef ee a0 c3 84 34 f2 b6 f6 d3 19 e1 f9 86 5f a4 50 2e 68 8a f2 03 39 85 15 af e3 dd cb 90 0f b9 f1 78 7a b6 74 1b e5 7d 07 a2 ef 1b 2a 01 ae 96 0d e2 5b 72 af 92 a1 ce 18 dc 6d 1e 1b 7f f7')
while True:
data, address = serv_sock.recvfrom(4096)
#data = str(data.decode('UTF-8'))
if naunce[0] == data[15]:
continue
naunce[0] = data[15]
response[15] = data[15]
data = data.hex(' ')
print('Received ' + str(len(data)) + ' bytes from ' + str(address) )
print('Data:' + data)
print('responding...')
sent = sock.sendto(response, response_add)
print('Sent confirmation back')Wrapping It Up
To recap the key security vulnerabilities addressed in this post:
- Discovery via Broadcast: Many inexpensive managed switches are vulnerable to discovery through specially crafted Ethernet broadcasts. This allows an attacker to identify the switch’s management IP address and potentially exploit any weaknesses.
- Firewall Limitations: Firewall rules cannot reliably restrict access to the management IP address. Any device capable of modifying its IP/subnet can connect and attempt to exploit vulnerabilities or brute-force login credentials.
- Lack of Logging: Most budget-friendly switches lack a failed login log, meaning a rogue device could repeatedly attempt to brute-force your credentials for an extended period – potentially years – without detection.
Despite the vulnerabilities present in these inexpensive switches, you can significantly reduce your risk. A well-configured, segregated network with robust firewall rules offers substantial protection against common attacks, including browser-based JavaScript attacks targeting network infrastructure. Below is a quick list of recommendations to help you secure your network.
- Isolate the Switch’s IP: Configure the managed switch’s IP address outside of any client subnet. This forces traffic to the management page through your router, allowing firewall rules to protect your network.
- Implement Strong Credentials: Use strong, unique usernames and passwords for the managed switch. Access to the switch grants the attacker the ability to modify VLAN IDs and potentially gain deeper access to your network.
- Secure VLAN Configuration: Properly configure your VLANs to prevent VLAN hopping – an attack that exploits VLAN tags to access unauthorized networks.
- Monitor for Suspicious Activity: Track network traffic, paying close attention to failed login attempts. Consider deploying a honeypot to detect and alert you to malicious activity.
- Migrate IOT Devices: If your network typology and budget allows consider placing remotely managed devices, such as IOT devices, on a more secure networking device – without these security issues.
Hopefully, this has highlighted the critical importance of thoroughly scrutinizing every device you introduce into your network. Don’t assume that a product’s security claims are sufficient – appearances can be deceiving, and a ‘security product’ doesn’t automatically guarantee protection. However, for home network security, the primary goal is often to increase the difficulty for an attacker – and with proper configuration, you’ll likely be well-protected.